Date: 19/7/2023 | Prepared by: Milan Patel, Associate Level 3 and DFIR Analyst
This alert aims to bring attention to a critical security issue that affects the NetScaler ADC and NetScaler Gateway (Formerly known as Citrix ADC and Citrix Gateway).
Three different vulnerabilities have been identified, among which the most severe vulnerability is being tracked with the following Common Vulnerabilities and Exposures (CVE) identifier: CVE-2023-3519.
On 18 July 2023, Citrix published a security bulletin warning customers of three newly identified vulnerabilities that affect NetScaler ADC and NetScaler Gateway.
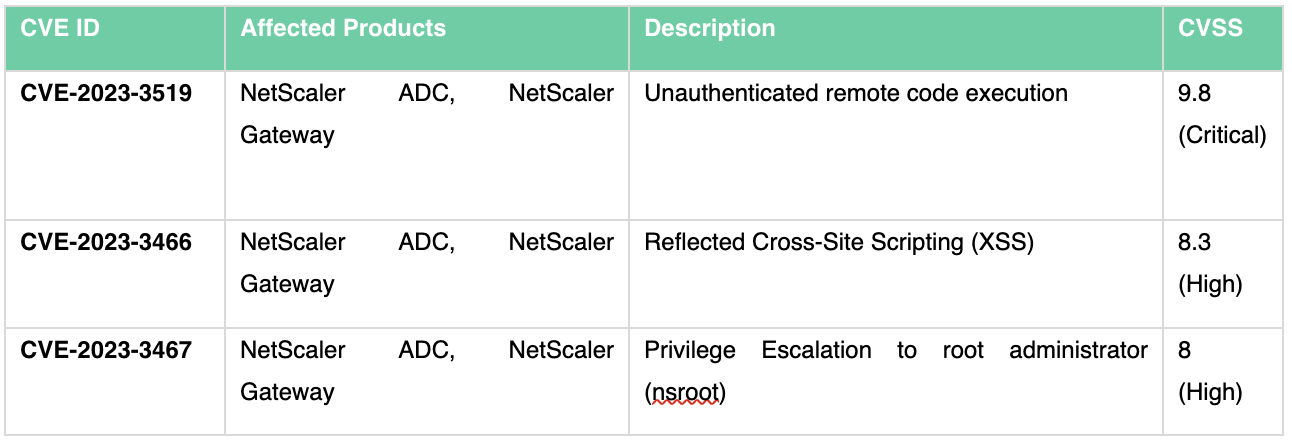 CVE-2023-3519 is an RCE vulnerability in NetScaler ADC and NetScaler Gateway. A remote, unauthenticated attacker can exploit this vulnerability to execute arbitrary code on a vulnerable server.
CVE-2023-3519 is an RCE vulnerability in NetScaler ADC and NetScaler Gateway. A remote, unauthenticated attacker can exploit this vulnerability to execute arbitrary code on a vulnerable server.
For a target appliance to be vulnerable to exploitation, it must be configured as a Gateway (e.g. VPN, ICA Proxy, CVP, RDP Proxy) or an AAA virtual server.
The vulnerability is rated as critical, and Citrix reports that “Exploits of CVE-2023-3519 on unmitigated appliances have been observed.”
CVE-2023-3466 is a reflected cross-site scripting (XSS) vulnerability, and successful exploitation can be achieved if a victim accesses an attacker-controlled link in their browser whilst also being on a network with connectivity to the NetScaler IP (NISP), such as through a phishing attack.
CVE-2023-3467 is a vulnerability that allows an attacker to elevate privileges to those of a root administrator (nsroot). Leveraging this flaw requires authenticated access to the NetScaler appliances IP address (NSIP) or a SubNet IP (SNIP) with access to the management interface.
This product line is a common target for Threat Actors due to the level of access granted to environments, and Triskele Labs expects exploitation to increase rapidly.
At the time of writing, technical details on how to leverage this vulnerability and proof-of-concept exploits are not publicly available. However, it has been evidenced that this zero-day has been known since the first week of July, and Citrix have observed attempts to leverage this exploit in the wild.
Successful exploitation of any of these vulnerabilities could result in an adversary achieving complete control of vulnerable Citrix appliances, allowing lateral movement into an environment. From there, a Threat Actor could exfiltrate data or deploy ransomware.
Customers with NetScaler ADC and Gateway appliances should update these devices as a matter of priority, as this will prevent Threat Actors from being able to exploit these vulnerabilities and gain access to corporate environments.
The following supported versions of NetScaler ADC and NetScaler Gateway are affected by the vulnerabilities:
Note: NetScaler ADC and NetScaler Gateway version 12.1 is now End of Life (EOL) and is vulnerable. As these devices are in EOL status, security updates to close this vulnerability will not be provided by Citrix.
This vulnerability only applies to non-Citrix-managed NetScaler ADC and NetScaler Gateway, as Citrix-managed cloud services or adaptive authentication customers are not vulnerable and do not need to take any action.
Citrix has observed attempts to exploit CVE-2023-3519 against unpatched appliances in the wild. Triskele Labs strongly urges affected customers of NetScaler ADC and NetScaler Gateway to install the relevant updated versions as soon as possible. The patched versions are listed below:
Note: NetScaler ADC and NetScaler Gateway version 12.1 is now End of Life (EOL). Customers are recommended to upgrade their appliances to one of the supported versions that address the vulnerabilities, as security updates will not be made available for End of Life appliances.
Detection rules have yet to be developed at the time of writing due to no public exploits or technical details being available; however, Triskele Labs Detection Engineers are monitoring the situation closely and will develop detection rules as more information becomes available.
Triskele Labs DefenceShield Security Operations Centre (SOC) is continuously monitoring for suspicious activity for Managed Detection and Response (MDR) clients.
Triskele Labs are performing ongoing scanning for DefenceShield Assess clients to detect vulnerable devices within client networks.
Customers should consider implementing the following mitigating controls, if not already:
For any questions, please contact DefenceShield SOC or Triskele Labs support.