Published Date: 22/03/2022
The purpose of this blog post is to bring attention to CRITICAL vulnerabilities present in Veeam Backup and Replication, an enterprise backup solution.
These vulnerabilities result in an unauthenticated Remote Code Execution (RCE) and a privilege escalation to SYSTEM for attackers. Active exploitation of this vulnerability has not yet been observed by Triskele Labs however may occur in the future.
On 12 March 2022, Veeam issued a notification describing critical vulnerabilities known as CVE-2022-26500 and CVE-2022-26501 present in Veeam Backup and Replication. The Veeam notification indicates that these CVEs have a CVSS v3 Score of 9.8, making them CRITICAL.
CVE-2022-26500 allows for unauthenticated Remote Code Execution (RCE) on Veeam Backup and Replication systems, which can result in malicious code being executed without the requirement for authentication. CVE-2022-26501 is a local Privilege Escalation vulnerability present in Veeam Backup and Replication systems that allows an attacked to escalate their privilege to SYSTEM level.
These vulnerabilities grant Threat Actors the ability to install malicious software and webshells or perform other malicious actions.
It is understood that these vulnerabilities are present in the following versions of Veeam Backup and Replication:
The Triskele Labs CTI team advises that Proof-of-Concept (POC) code exploiting the vulnerability is not yet publicly available however is being discussed online by the researcher that responsibly disclosed the vulnerabilities to Veeam:
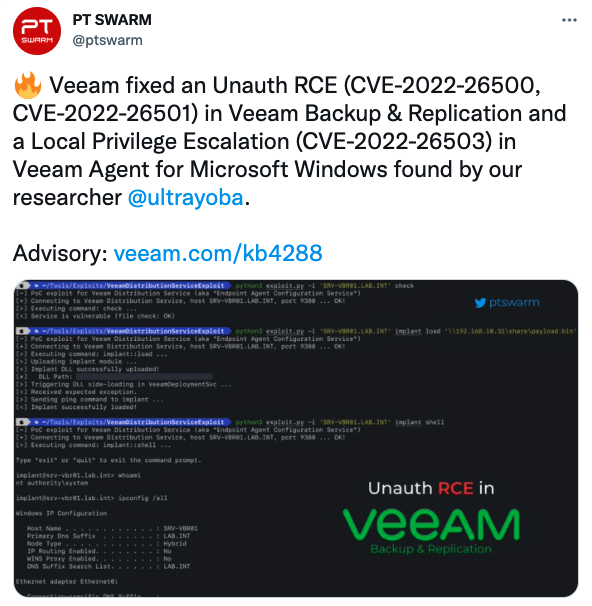
Source: https://twitter.com/ptswarm/status/1503360681978077185
It is apparent that the researcher has developed a tool for efficient and easy detection and exploitation of the vulnerabilities, however, has yet to publish it.
If this tool were to be publicly released it would enable Threat Actors a direct route to exploiting vulnerable versions of Veeam backup and Replication in the wild.
If you are utilising any version of Veeam Backup and Replication excluding versions 11 and 10 installed using the ISO images dated 2022-03-02 or later, install the latest patch, available here - https://www.veeam.com/kb4288
Triskele Labs are continually monitoring for suspicious activity within customer environments.
Deployed SIEM and EDR agents on all servers and endpoints will aid in detecting a Threat Actor successfully exploiting this vulnerability in an environment and commencing reconnaissance.
References used for the generation of this release: